Introduction
In the upcoming weeks we will be posting new videos to the SAP HANA Academy to show new features and functionality introduced with SAP HANA Support Package Stack (SPS) 11.
* What's New with SAP HANA SPS 11 - by the SAP HANA Academy
The topic of this blog is security.
SAP HANA Academy - SAP HANA SPS 11: What's New? - Security - YouTube
What's New?
In the upcoming weeks we will be posting new videos to the SAP HANA Academy to show new features and functionality introduced with SAP HANA Support Package Stack (SPS) 11.
* What's New with SAP HANA SPS 11 - by the SAP HANA Academy
The topic of this blog is security.
SAP HANA Academy - SAP HANA SPS 11: What's New? - Security - YouTube
Security Administration with SAP HANA Cockpit
Two new groups have been added to the SAP HANA cockpit
- Security Overview
- Certificate Management
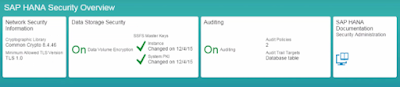
With Security Overview, you can monitor critical security settings:
- Network Security Information - displays cryptographic library and TLS settings
- Data Storage Security - displays status of data encryption and last change of the SSFS master keys
- Auditing - displays status of audit logging, policies and trail target
The Data Storage Security app and the Auditing app also allow for configuration of data volume encryption and auditing, respectively.
With Certificate Management, you can now use the Certificate Store and Certificate Collection apps to perform all certificate management tasks:
- Import X.509 client certificates into the certificate store
- Create certificate collections
- Add trusted certificates and server certificates to collections
- Set the purpose of collections
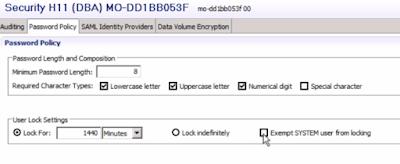
Password Policy
Three new parameters have been added to the password policy:
- force_first_password_change
- password_lock_for_system_user
- detailed_error_on_connect
CREATE USER <user_name> PASSWORD <password> [NO FORCE_FIRST_PASSWORD_CHANGE]
Parameter password_lock_for_system_user specifies whether or not the user SYSTEM is locked after the maximum number of failed logon attempts. The default value is true. The Security editor of the SAP HANA studio supports this setting but not yet in the Web-based Development Workbench (use SQL).
Parameter detailed_error_on_connect configures the detail level of error information returned when a logon attempt fails. The default value is false, which means that only the information authentication failed is returned. If this parameter is set to true, the exact reason for authentication failure is output
- Invalid user password
- User is locked
- Connect try is outside validity period
- User is deactivated
Encryption
There was some ado last summer about the static encryption keys that were included with SAP HANA. See for example: SAP HANA security: Static encryption keys as the latest trend - ERPScan. Although the Security Configuration Checklist in the SAP HANA Security guide always clearly stated to change these keys prior to usage, alas not everyone was informed of this.
To make encryption both more secure and easier to use, the following changes have been implemented:
- The initial master keys of the instance Secure Storage on the File System (SSFS) and the system PKI SSFS are now changed automatically after installation or upgrade. These keys are used for data storage and network encryption.
- The initial default encryption key of the secure user store (hdbuserstore) is now automatically changed when the first entry is created. This store is the client-side tool for storing user logon information for connecting to an SAP HANA system, used for example for ODBC/JDBC connections for application servers, backup scripts, etc.
- Communication encryption between SAP HANA processes (database engine, name server, application server, etc.) is now automatically enabled when internal communication in a multiple-host SAP HANA system is activated.
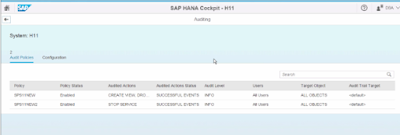
Auditing
For data management purposes, you can now delete all audit entries in the database table used as audit trail target with SQL.
ALTER SYSTEM CLEAR AUDIT LOG ALL
This is for those exceptional cases that the table has grown so large that there is not enough memory to delete old entries. Better of course would be to do some regular monitoring of your audit tables!
The following user actions in SAP HANA can now be audited:
- CREATE / DROP PROCEDURE
- CREATE / DROP VIEW
- STOP SERVICES
SAP HANA Multitenant Database Containers
You can now configure TLS/SSL keys and certificates for communication with HTTP clients per tenant database. See Configure HTTP(S) Access to Multitenant Database Containers - SAP HANA Administration Guide - SAP Library for how to set this up.
SQL Security Functions
Three new security functions have been added:
- ESCAPE_DOUBLE_QUOTES
- ESCAPE_SINGLE_QUOTES
- IS_SQL_INJECTION_SAFE
They ensure that a valid SQL identifier is used in dynamic SQL statements to prevent SQL injections.
01. SELECT ESCAPE_DOUBLE_QUOTES('TAB"LE') "table_name" FROM DUMMY
02. table_name
03. TAB""LE
SAP Security Baseline Integration
Integration of SAP HANA into SAP Security Baseline, Early Watch Alert and Configuration Validation has been improved. The checks were first delivered with the SAP Solution Manager Plug-In ST-SER 620_2005_1 and they have been revised several times since then. See SAP Note: 863362 - Security checks in SAP EarlyWatch Alert, EarlyWatch and GoingLive sessions
Source: scn.sap.com

No comments:
Post a Comment