I have been seeing a growing number of security related questions from customers. This blog will cover step-by-step configuration of SSL for internal communication and system replication. I hope this will help you guys out.
Security is one of the most significant feature any product should posses. In SAP HANA, we can precisely configure both internal and external communication.
Here we will be seeing how to configure server-side SSL manually, when you do not want to use the default system PKI (public key infrastructure). In most cases customer wanted to create their own certificate and use it for internode communication and for System Replication.
Things to know…
◉ In a multi-host system, every host requires a public and private key pair and a public-key server certificate
◉ Use CommonCrypto library (libsapcrypto.so) as the cryptographic library which should be installed as part of SAP HANA server installation
◉ For HANA 1.00, In-Database configuration is not supported for internal communication between servers and for system replication communication.
◉ OpenSSL can be used to create server certificate. With CommonCryptoLib, you can also use SAP Web dispatcher administration tool or SAPGENPSE tool.
◉ Do not password protect keystore file which contains servers private key.
1. Create server certificate
2. Self-sign the certificate
3. Import keystore and public certificate into each host
Please note:
The recommendation from SAP is to use a private CA for each host, but here I will only show how to create certificate and sign them in one host. You will just need to follow the same steps in other hosts if you are using multi-host environment.
I am here using a 3 node system, MN1, vandevvmlnx011/012/013.
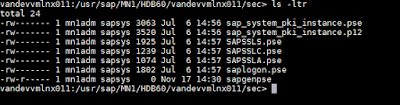
1. Go to /sec directory in the host machine, here starting with node vandevvmlnx011, path: /usr/sap/<SID>/HDB<INSTANCE_NUMBER>/<HOST_NAME>/sec
2. Use OpenSSL tool to request for a root certificate, using command:
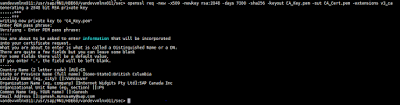
/usr/sap/MN1/HDB60/vandevvmlnx011/sec> openssl req -new -x509 -newkey rsa:2048 -days 7300 -sha256 -keyout CA_Key.pem -out CA_Cert.pem -extensions v3_ca
This will ask you to enter PEM pass phrase, I used my SYSTEM user password for test, you may use it per your convenience. Also have to enter other details like country, state, locality etc.
Security is one of the most significant feature any product should posses. In SAP HANA, we can precisely configure both internal and external communication.
Here we will be seeing how to configure server-side SSL manually, when you do not want to use the default system PKI (public key infrastructure). In most cases customer wanted to create their own certificate and use it for internode communication and for System Replication.
Things to know…
◉ In a multi-host system, every host requires a public and private key pair and a public-key server certificate
◉ Use CommonCrypto library (libsapcrypto.so) as the cryptographic library which should be installed as part of SAP HANA server installation
◉ For HANA 1.00, In-Database configuration is not supported for internal communication between servers and for system replication communication.
◉ OpenSSL can be used to create server certificate. With CommonCryptoLib, you can also use SAP Web dispatcher administration tool or SAPGENPSE tool.
◉ Do not password protect keystore file which contains servers private key.
High Level Overview:
1. Create server certificate
2. Self-sign the certificate
3. Import keystore and public certificate into each host
Please note:
The recommendation from SAP is to use a private CA for each host, but here I will only show how to create certificate and sign them in one host. You will just need to follow the same steps in other hosts if you are using multi-host environment.
Create root certificate:
I am here using a 3 node system, MN1, vandevvmlnx011/012/013.
1. Go to /sec directory in the host machine, here starting with node vandevvmlnx011, path: /usr/sap/<SID>/HDB<INSTANCE_NUMBER>/<HOST_NAME>/sec
/usr/sap/MN1/HDB60/vandevvmlnx011/sec> openssl req -new -x509 -newkey rsa:2048 -days 7300 -sha256 -keyout CA_Key.pem -out CA_Cert.pem -extensions v3_ca
This will ask you to enter PEM pass phrase, I used my SYSTEM user password for test, you may use it per your convenience. Also have to enter other details like country, state, locality etc.
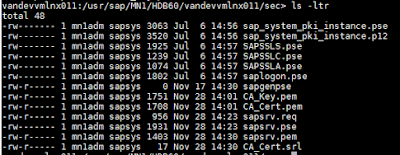
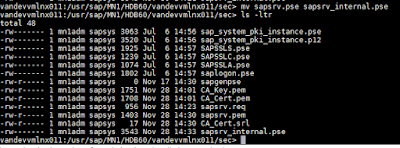
3. This should have created two new files CA_Key.pem and CA_Cert.pem
Creating server certificate:
1. Here I use sapgenpse, which is installed with HANA installation, to create server certificate request. sapsrv.pse is the name of the certificate we are requesting for and so make sure there is no file with the same name available in that path. Command used:
/usr/sap/MN1/HDB60/vandevvmlnx011/sec> sapgenpse gen_pse -p sapsrv.pse -r sapsrv.req CN=”*.xxxx.xxxx.sap.corp”,O=”HANA Support”,C=”US”
Very important…
◉ Do not enter password when requested for PSE PIN/passphrase as it is not supported!
◉ Also, to secure internal communication, canonical name should be host specific, eg CN=”<hostname_with_domain>”. So when creating private CA on each host, parameter CN will be unique. But here in this example below, I specified CN=”*.xxxx.xxxx.sap.com”, which is good for system replication scenario, but not for internal communication between hosts.
2. This should have created new files sapsrv.req and sapsrv.pse
Self signing certificate request:
1. Here again using OpenSSL to self sign the certificate sapsrv.req with command:
/usr/sap/MN1/HDB60/vandevvmlnx011/sec> openssl x509 -req -days 7300 -in sapsrv.req -sha256 -extfile /etc/ssl/ope-out sapsrv.pem
Note: You can also get this signed through your CA, if doesn’t want to self-sign it.
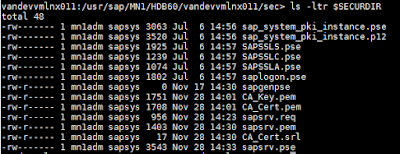
2. A new file with name sapsrv.pem will be created in the same directory, $SECURDIR
Importing server certificate:
1. Import the signed certificate into file sapsrv.pse using sapgenpse utility as below:
/usr/sap/MN1/HDB60/vandevvmlnx011/sec> sapgenpse import_own_cert -c sapsrv.pem -p sapsrv.pse -r CA_Cert.pem
2. You can see the file sapsrv.pse is updated from timestamp
Copying file to other nodes…
Please note that a private certificate have to be created for each host in the multi-host system. So follow the same steps that we did above to create a sapsrv.pse file and sign & import it, in other hosts as well.
Now re-naming saprv.pse file to sapsrv_internal.pse in all three nodes. For example in node 011:
Configuration in HANA Studio (global.ini):
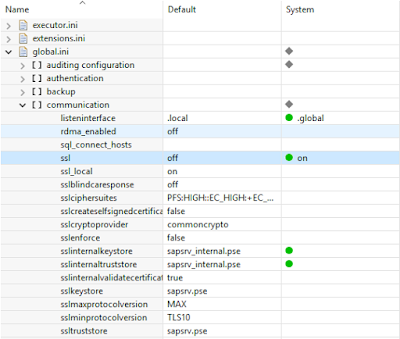
1. Open HANA Studio, go to Administration Console -> Configuration -> global.ini -> communication
2. Set value for parameter ssl = on and make sure sslinternalkeystore and sslinternaltruststore has correct file pointed to.
3. sapsrv_internal.pse is the file we created and so the parameters sslinternalkeystore and sslinternaltruststore has that value.
For System Replication:
In case to secure communication for system replication, primary and secondary each will have one .pse file only. When creating the server certificate, we provide the canonical name (like CN=” *.prod.sap.com”), which should be same for both primary and secondary.
So when creating certificate for system replication scenario, no need to have separate .pse file for each host.
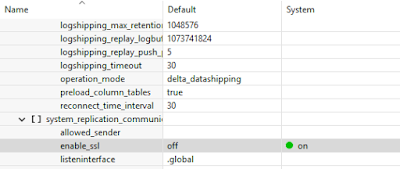
Communication between sites (metadata and data channels) require the same configuration as we did above in global.ini/[communication] section. However to secure data communication, we must set parameter enable_ssl = on, under section [system_replication_communication] of global.ini file.
All these changes in global.ini file requires a complete database restart as below:
>sapcontrol -nr <instance_number> -function StopService
>sapcontrol -nr <instance_number> -function StartService
Now communication between hosts and communication between sites in system replication scenario are all secured using SSL.


Really nice blog and impressive information you gave us.Thank you and i will expect more in future.
ReplyDeleteJAVA Training in Chennai
Best JAVA Training institute in Chennai
Python Training in Chennai
Selenium Training in Chennai
Android Training in Chennai
Big data training in chennai
JAVA Training in Chennai
Java Training in Tambaram