Introduction
Investigative Case Management (ICM) is now available on SAP S/4HANA since 1909 FPS00 release.
Data Protection and Privacy
ICM provides specific features and functions to support compliance with the relevant legal requirements and data protection and privacy.
Logging and Monitoring (Section-254 of Federal Data Protection Act, Germany)
ICM is mainly used by law-enforcement authorities, therefore logging and monitoring access to sensitive data is required by law in order to fulfill legal compliance. Following are the tools you can consider for fulfilling the logging and monitoring requirements:
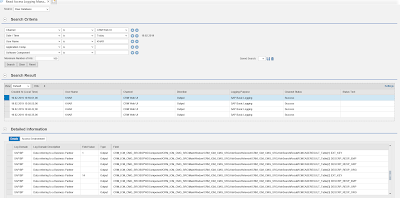
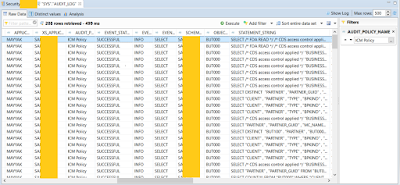
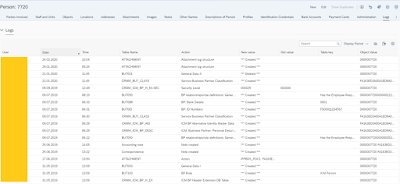
Read Access Logging: SAP delivers sample configurations for ICM through SAP Note 2739669. Investigative Case Management logs data of ICM person including the person search and results. It also logs data of ICM person that are displayed on the case, lead, activity, incident, object and locations overview pages. Different channels like Web client UI, SAP Gateway services, Backend transactions are covered in the RAL tool.
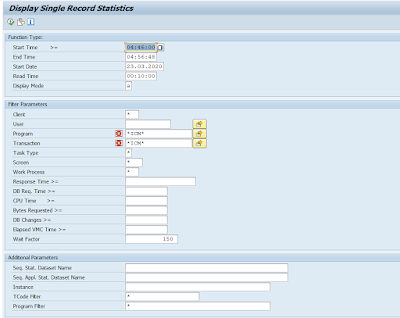
Work-load analysis for ICM: SAP workload analysis (transaction STAD) plays a vital role during security audits. Auditors often use this transaction to intersect any possible unauthorized system access. ICM provides a refined flavor of transaction STAD in a wrapper transaction called STAD_ICM. This aims at assisting auditors to provide flexible selection screens. A default variant DEFAULT_ICM for the selection screen provides a jump start for auditors to arrive at a positive list of un-authorized access in an ICM system context to readily act upon.
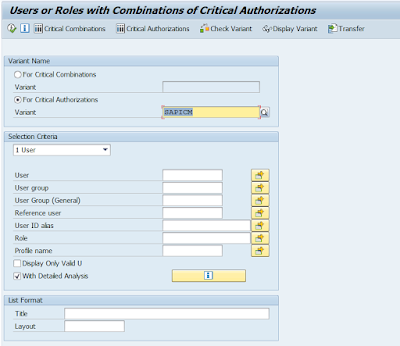
ICM Critical Authorizations for User Information System: SAP User Information System (transaction SUIM) summarizes many different SAP authorization aspects in one place.
To detect critical authorizations assigned to a user via a PFCG role, a new variant in the SAP User Information System (transaction SUIM) is created. The ICM variant SAPICM of the SUIM report “Users or Roles with Combinations of Critical Authorizations” (technical name of the report: RSUSR008_009_NEW) contains critical authorization objects which should not be accessible for users in the ICM. This variant allows to scan PFCG roles for the corresponding authorization objects which are marked as critical.
Auditing in SAP HANA systems: Auditing at HANA provides you with visibility on who did what in the database (or tried to do what) and when. This allows you, for example, to log and monitor read access to sensitive data at the database level against the application level. Administrator should enable this auditing in the production system to take advantage of the service.
Change log (Section-265 of Federal Data Protection Act, Germany)
All entities with in ICM supports standard Netweaver based change log feature. Fields of the standard tables are enabled for this feature. Any customer extended fields to be made sure they are change log enabled to be automatically included in the change log list.
Information Retrieval (Section-255 of Federal Data Protection Act, Germany)
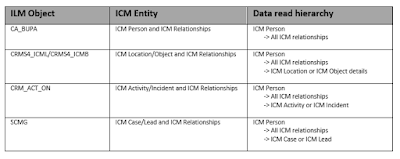
ICM supports information retrieval using SAP NetWeaver component Information Retrieval Framework (IRF). ICM delivers multiple IRF models which allow retrieval of ICM entity data with reference to an ICM person. Customers can enhance the model with their own namespace to include any extension to the standard data model.
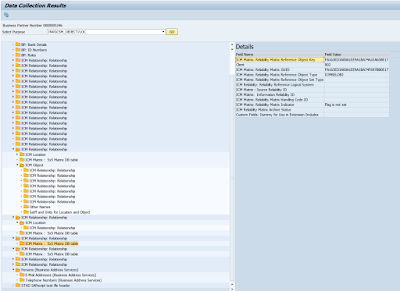
Below is the sample data collection result for Location or Objects related data subjects.
Archiving, Blocking and Deletion (Section-256 of Federal Data Protection Act, Germany)
ICM supports Information Life Cycle (ILM) based archiving, blocking and deletion features for all its entities including relationship data. Additionally, ICM provides specialized features called anonymizing person data and expunging of the relationships to control the life-cycle of data.
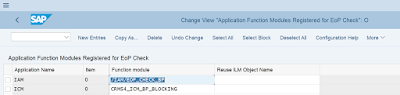
ICM-related EoP (End of Purpose) checks are made during the BP blocking process. In the customization, a new application named ICM along with a standard function module CRMS4_ICM_BP_BLOCKING has been registered to perform the check. This prevents ICM data from being accidentally blocked or deleted.
Customers can make user of the above tools and functions to comply with data protection and privacy laws for Investigative Case Management.
No comments:
Post a Comment