Introduction
We live in an exciting era where business is transforming at an unprecedented rate that we have not fully come to grasp its impact on data privacy. Look at the statistics which are staggering. Globally, smartphone penetration is estimated to be 8 billion smartphone subscriptions worldwide. An average smart phone user has 80 application on its phone and approximately 10 application are used daily. The mobile phone application collects enormous amount of personal data such as GPS location, IP addresses, voice, video, contact lists, text messages, passwords, call history. The e-commerce and service providers use advance digital technologies such as Artificial Intelligence, Machine Learning, Software Robotics to profile and process personal data. Realizing the impact of data privacy and harm it may cause to individuals and society, many countries globally have been enacting data privacy regulations.
In this blog, we explore perspectives on future of personal data privacy with trends and challenges ahead protecting individual rights and enabling innovating at the core of services.
Increasing Personal Data Privacy Conundrum
We are often faced with situation where we must divulge privacy information to get services we want. Every e-commerce site that we visit, mobile application we click, social media post that we like and contribute, inherently collects vast amount of data in the form of access to browser cookies, access to phone contacts, photos, videos, preferences, personal messages that it would be impossible for an individuals to comprehend data types being collected and how an individuals is profiled. While “choice and consent” may be offered, an individual is presented with a conundrum of choices, providing privacy information to get services an individual want. We face the dilemma of wanting to get desired services in exchange of personal data.
Read More: C_HANADEV_16 Key Points
Thus far, Article 4 of GDPR has defined “personal data” in a most elegant way as “any information relating to an identified or identifiable natural person” The word, “any” has a broad scope in nature.
In future, the scope of personal data definition may be broadened, given the capabilities of automated processing and profiling of an individual based on the number of parameters, bias, and algorithms. A seemingly, innocuous data with no linkage when combined may potentially link to an individual which may potentially be exploited to meet narrow ends beyond the stated purpose at the time of personal data collection.
Personal Data Types
Global Rise in Data Protection and Privacy Regulations
GDPR was a watershed moment in the history of data privacy when it came into force in May 2018, regulating how personal data must be collected and processed. Since then many countries globally began working on their own data protection regulations. For example,
◉ In APJ, while
Singapore PDPA was passed in October 2012, Singapore joins Asia‑Pacific Economic Cooperation Cross-Border Privacy Rules (
APEC CBPR) System in 2020.
◉ In Thailand PDPA became a law in 2019. Both in Malaysia and Philippines, amendments are being to their data protection regulations and applications of the data protection laws are being monitored closely for compliance.
Over the next 2-3 years, we will notice a growing trend where countries enacting personal data protection regulations. This brings an additional challenge on how cross-border data transfer can be done adhering to each of the countries data protection regulations.
The approach and philosophy of personal data privacy regulations vastly vary in tone and tenor between regions. It is well known that government is supreme in China retaining ability to have overarching powers and invasive data rights. While European Union protects the rights of individual data subjects under GDPR, US data privacy laws generally more in favor of large corporations and does not maintain great deal of federal level oversight on data privacy laws, maintaining laws enacted some at federal and state level with lack of consistency. In India, the
PDPB Bill in parliament is being debated intensely as it gives government of the day, an unlimited power to be an executive and adjudicator providing an open-ended exception for state surveillance.
In July 2020, European Union (CJEU) dismantled Privacy Shield agreement between the European Union (EU) and the United States since CJEU determined that the adequacy agreement failed to protect the privacy of its citizens’ data. Companies have been scrambled to find adequate alternate arrangements for such data transfer between US and EU.
GDPR maintains adequacy determination on data transfer outside the EU and onward transfer from or to a party outside the EU without requiring additional authorization from a national supervisory authority. APEC Privacy Framework has been built with similar approach for consumer, business, and regulator trust in cross border flows of personal data between APEC member countries.
Eventually, in future, adequacy arrangements must be worked out between countries/within the regions for global economies to flourish while maintaining reasonable data privacy.
Cross-Border Personal Data Transfer
Focus on Privacy Technologies
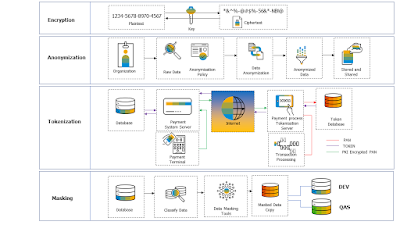
In future, many companies will invest in privacy technologies to keep up with regulatory compliance and to meet the compliance for processing the personal data. AI and Machine will be integrated in the data classifications, personal data processing, storage, transaction processing. Within the storage of the data in database, many privacy technologies such as anonymization, pseudonymization, tokenisation, masking would be used.
In many regulations, anonymized data eliminates any linkage to an identifiable individual and hence anonymized data is excluded from regulations as it is no longer considered as “personal data”. In addition, there would be greater need for homomorphic encryption, obfuscation, de-identification to drive governance and compliance imperatives for the organization.
Privacy Technologies
Automated Personal Data Processing with Artificial Intelligence and Machine Learning
In future, the intensity of AI and Machine Learning application will be on rise in making predictive analytics, profiling and decision making in industry applications such as stock market trading, human resources, medical, disease control, medical research, health care providers.
Organization gets personal data from multiple sources and in future profiling by automated means can become a norm, given the volume, velocity, and variety of data. This will be enhanced and achieved through technologies such as Artificial Intelligence (AI), Machine Learning (ML). The profiling is done via smart algorithms that makes automated decision that includes predicting behaviors, offering specific range of services for certain profiles, collecting, and correlating various data sources.
Inadvertently, this may lead to AI “bias” in decision making due to data set that is fed into systems. This may lead to violation of equal opportunity and may threaten social cohesion due to inequality. Regulators are weary of potential risks and opportunities with use of AI and ML and are moving in the direction of regulating processing of personal data with AI and ML technologies.

AI and ML Bias
Rise in personal data collection for tracking during pandemic
As the world reels under the effect of pandemic (COVID-19), responsible government around the world have put in measures with contact tracing application that collects personal data, GPS, places visited, time spent at each places, individuals in communications via blue tooth signals. While purpose limitation and collection limitation principles may have been applied, it is not entirely transparent if the data will be processed by the governments for any other reasons. There has always been a conflict that exists between protecting public health vs protecting personal data privacy.
Despite best of measures put forward by the government to protect personal data of the populations, cyber risk is at the peak now, given the spam, phishing, ransomware, social engineering, malware masquerading, sophisticated and organized cyber-attacks perpetuated by cyber threat actor is on rise, posing greater risks to individuals.
SAP Data Privacy Contracts, Tools and Audits
We turn our attention, in this section, on how SAP handles personal data protection at multiple levels – contractual assurance, data privacy by default and by design in cloud applications and security assurance via independent 3rd party privacy audit and certifications.
Contractual Assurance:
SAP is committed to help our customers to be compliant to data protections regulations. As a data processor, SAP provides contractual assurance via
Personal Data Processing Agreement for SAP Cloud Services and comply to data protection regulations to an extent applicable for SAP cloud services.
SAP Cloud Applications – Privacy by Design and Privacy by Default
SAP Cloud Applications operating on a SaaS model have many built-in data protection and privacy features that can be configured by customers. SAP supports privacy by design and privacy by default concept. This includes configuration on consent management, read access logging, change log, security audit logs, data deletion and retention rules, data subject information reporting, encryption at all levels – Data Encryption in Transit, Data at Rest Encryption (DB Volume), Columnar Encryption, Application Encryption, Backup Encryption. Customers have access to application level data privacy and protection configurations to enable them to configure privacy settings based on their privacy policies.
Security and Privacy Tools
SAP supports several data protection and privacy tools that can be integrated into cloud applications and may be available as an additional subscription or enabling them as a part of cloud bundle. Few of the tools are listed here:
SAP UI Data Protection Masking: This tool conceal data, reveal on demand with proper authorization
SAP Identity Access Governance: This service help to provides Access Governance, access analysis, role design, access request, access certification, and privilege access management.
Identity Authentication Service (IAS): This services helps to authenticate and manage users
Identity Provisioning Service (IPS): Allows the provisioning of centrally managed identities and their access across the enterprise.
SAP Data Custodian: SAP Data custodian offers full stack transparency and control which includes infrastructure, operating systems, databases, SAP enterprise applications.
SAP Data Custodian KMS offers Customer Controlled Key Management Service
SAP Data Retention Manager: This tool help to manage retention and residence rules to block or destroy personal data and related transactional data for applications
Audits and Certifications:
SAP cloud services are audited for BS10012:2017 privacy standards. This is a British standard providing best practice framework for a personal information management system that is aligned to the principles of the EU GDPR. Many of SAP cloud services have achieved with compliance to norms of ISO 27018 , an international standard created specifically for data privacy in cloud computing. The full certification and compliance can be found
here
Source: sap.com



No comments:
Post a Comment