Obtaining the Software
It’s easy to forget exactly what’s been installed, so I have captured here the pieces I needed.
| Search Words | Description | Filename (as at 11-Sept-2018) |
| EXTAPPSER | Extended App Services – XSA server binaries | EXTAPPSER00P_88-70001316.SAR |
| HRTT | HANA Run Time Tools, required for WebIDE | XSACHRTT06_62-70002322.ZIP |
| XSACMONITOR | XSA Monitoring, required for WebIDE | XSACMONITORING06_5-70002324.ZIP |
| WEBIDE | SAP WEBIDE 2 | XSACSAPWEBIDE03_6-80002257.ZIP |
Extracting the SAR
If you extract the XSA Server (EXTAPPSER*.SAR) component to a sub-folder within the same parent directory as the install media (SAP_HANA_DATABASE) then the SAP_HANA_DATABASE\hdblcm will find EXTAPPSER.
media
|
|– SAP_HANA_DATABASE
| |- hdblcm
| |- hdbinst
| |- hdbsetup
| |- …
|
|– XSA_SERVER (put EXTAPPSER*.SAR in here, and extract it)
| |- hdbinst
| |- …
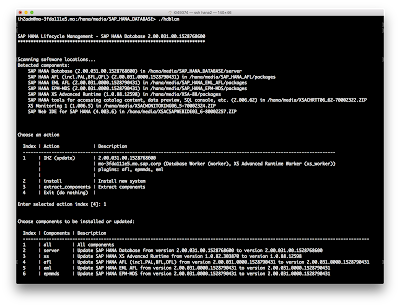
Installing EXTAPPSER
Running hdblcm from SAP_HANA_DATABASE directory and it will automagically find the XSA_SERVER and other packages within the directory structure.
Below I had already installed the XSA update using option 3.
Updating the XSA Apps
With the install completed I then used the xs client commands to update the WebIDE and associated components.
First log into XSA and specifying the appropriate space.
mo-3fda111e5.mo:/usr/sap/IH2/HDB00> xs login -u XSA_ADMIN -p TopSecretPassword -a https://mo-3fda111e5.mo.sap.corp:30030 -s SAP
API_URL: https://mo-3fda111e5.mo.sap.corp:30030
USERNAME: XSA_ADMIN
Authenticating...
ORG: orgname
SPACE: SAP
API endpoint: https://mo-3fda111e5.mo.sap.corp:30030 (API version: 1)
User: XSA_ADMIN
Org: orgname
Space: SAP
I can now go ahead an install the download zip files.
xs install XSACHRTT06_62-70002322.ZIP
xs install XSACSAPWEBIDE03_6-80002257.ZIP
xs install XSACMONITORING06_5-70002324.ZIP
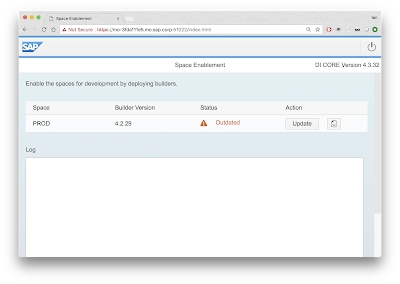
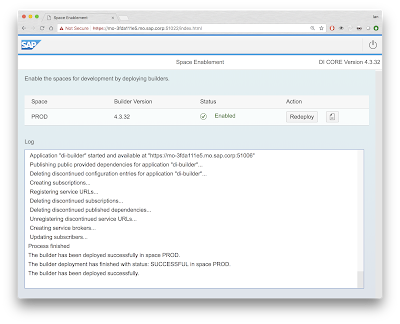
Space Enablement
Before actually using the updated WebIDE, it is required update the di-builder via the space enablement your non SAP space. To find out out the URL for this you can run this xs command.
mo-3fda111e5.mo:/hana/media/XSA-88> xs app di-space-enablement-ui --urls
https://mo-3fda111e5.mo.sap.corp:51022
Going to that URL,shows the space needs updating with the latest goodies.
Proxy Configuration
For me to use external sites such as github.com or deploy to cloudfoundary required a proxy. This can done by specifying the JBP_CONFIG_JAVA_OPTS for the DI_CORE module and redeploying it. I created a .mtaext file with the following contents.
_schema-version: "3.1.0"
ID: com.sap.devx.xs2-config1
extends: com.sap.devx.webide
modules:
- name: di-core
parameters:
port: 53030
memory: 512M
properties:
JBP_CONFIG_JAVA_OPTS: '[java_opts: " -Dhttps.proxyHost=proxy.wdf.sap.corp -Dhttps.proxyPort=8080 -Dhttp.proxyHost=proxy.wdf.sap.corp -Dhttp.proxyPort=8080 -Dhttp.proxyHost=proxy.wdf.sap.corp -Dhttp.proxyPort=8080 -Dhttp.nonProxyHosts=\\"*.sap.corp;*.corp.sap;mo-3fda111e5;mo-3fda111e5.mo.sap.corp;localhost;127.0.0.1;10.*\\" -Dhttps.nonProxyHosts=\\"*.sap.corp;*.corp.sap;mo-3fda111e5;mo-3fda111e5.mo.sap.corp;localhost;127.0.0.1;10.*\\""]'
After creating the .mtaext file I then needed to redploy the WebIDE to pickup the proxy settings.
xs install XSACSAPWEBIDE03_6-80002257.ZIP -e My-WebIDE.mtaext -o ALLOW_SC_SAME_VERSION --delete-services
Npm (node package manager) also requires the proxy to be set, I did this as below.
xs set-env di-local-npm-registry HTTPS_PROXY http://proxy.wdf.sap.corp:8080
xs set-env di-local-npm-registry HTTP_PROXY http://proxy.wdf.sap.corp:8080
xs restage di-local-npm-registry
xs restart di-local-npm-registry
SSL – Private Key
Previously I had not configured a trusted SSL certificate for XSA, but this can lead to unexpected errors with the different xsa services. Each untrusted URL needs to been granted browser exceptions.
I had already setup SSL for XS, so thought it would be easy to re-use some of that configuration (it’s not that easy).
1. Export the private key from the in-built SAP keystore.
sapgenpse export_p12 -p /usr/sap/IH2/HDB00/mo-3fda111e5.mo.sap.corp/sec/SAPSSLS.pse /hana/media/ssl/Export.p12
2. Convert the .p12 format to pem.
openssl pkcs12 -in Export.p12 -out Export.pem -nodes
Within the newly generated export.pem there are multiple certificates and keys. The Private Key is the required part which starts with.
—–BEGIN PRIVATE KEY—–
3. copy/paste just the private key that into a new file Private.key
4. Convert to pkcs8 (that XSA requires). This can be converted with this command.
openssl pkcs8 -topk8 -in Private.key -out Private_pkcs8.key -nocrypt
SSL Root & Intermediate Certificates
XSA also requires a full certificate chain. This means you need to supply the host, intermediate and root certificates all combined into a single x.509 PEM encoded file.
I was provisioning and internal SAP host using our internal Web Enrolment Service. This provides the certificate for the XSA host, but it needs to converted and combined with the full certificate chain. I download the appropriate root (SAP Global Root CA) and intermediate (SAPNetCA_G2), which come in .crt format.
1. Download the correct root & intermediate Certificates
2. Convert to x509 PEM format
openssl x509 -in SAPGlobalRootCA.crt -outform PEM -out SAPGlobalRootCA.pem
openssl x509 -in SAPNetCA_G2.crt -outform PEM -out SAPNetCA_G2.pem
openssl x509 -in mo-3f.txt -outform PEM -out mo-3f.pem
3. Combine certificates in correct order (host, intermediate, root)
cat mo-3f.pem >> combined.pem
cat SAPNetCA_G2.pem >> combined.pem
cat SAPGlobalRootCA.pem >> combined.pem
Upload to XSA
xs set-certificate mo-3fda111e5.mo.sap.corp -c combined.pem -k Private_pkcs8.key
After successfully installing the certificate you need to restart each of the XSA apps individually or the whole of XSA (which is easier). This can be dome with the hdbadm user.
mo-3fda111e5.mo:/usr/sap/IH2/HDB00> XSA restart
After which I have XSA & WebIDE running with a signed SSL certificate.
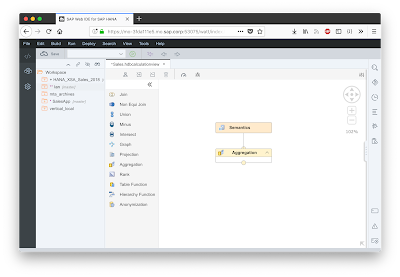
Including all the new graphical Calculation View operators like graph, anonymization, union, minus, intersect, hierarchy function, etc.
Troubleshooting
If you do experience any issues the following commands are useful for identifying, potential issues.
xs display-installation-logs
xs logs webide —recent
If the certificates get messed up you can reset those using the hdbadm user
mo-3fda111e5.mo:/usr/sap/IH2/HDB00> XSA reset-certificate

No comments:
Post a Comment