In this blog, we explore how dedicated private connectivity between SAP HANA Enterprise Cloud running on AWS and on-premise data center can be achieved. Presently, there are two options for customers to connect from their on-premise data center to SAP HANA Enterprise Cloud.
● Site-to-Site VPN Tunnel
● AWS Direct Connect
Challenges with Site-to-Site VPN are as follows:
From a security and compliance perspective, many government and public sector organization do not allow public internet to access critical business application over the internet. This is one of the biggest limitations and impediments to meeting regulatory compliance requirements. Besides, typically site-to-site VPN offers very limited non-guaranteed bandwidth, typically 1Gbps per tunnel. As the traffic via Internet traverse via multiple internet router hops, it is expected that there would be higher latency traversing over public network.
While many customers find Internet services today to be highly stable and are comfortable running IPSEC VPN between their on-premise and SAP HANA Enterprise Cloud on AWS VPC, exposing selective business process/applications over the IPSEC VPN tunnels over the Internet, we recognize that few of our regulated customers consider AWS VPC that is hosting SAP HANA Enterprise Cloud as an extension of their on-premise data center and hence require dedicated private connectivity to SAP HANA Enterprise Cloud.
SAP HANA Enterprise Cloud Connectivity via AWS Direct Connect
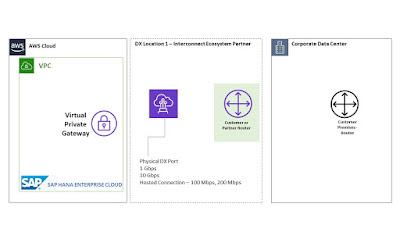
AWS offers Direct Connect services which is a physical connection that connects customer on-premise network to AWS. This allows customer traffic to traverse via private network without traversing via Internet and offers an excellent bandwidth, consistent performance and low latency. The connectivity architecture has three parts:
Step 1
● SAP manages Virtual Private Cloud that hosts SAP HANA Enterprise Cloud for customers in AWS. Therefore, SAP will obtain Letter of Authorization and Connecting Facility Assignment (LOA-CFA) from AWS. As a part of this configuration SAP will provide DX name, location, port speed and interconnect partner on the AWS portal. This is a “AWS DX port” operating at certain speed belonging AWS Account ID managed by SAP
Step 2:
● SAP will provide LOA-CFA to customer who will work with their interconnect local provider. Customer works with Interconnect Provider (such as Equinix, Verizon) to “cross connect” AWS DX port in DX location to customer router/partner router in the same DX location. Connections to AWS Direct Connect require single mode fiber, 1000BASE-LX (1310nm) for 1 gigabit Ethernet, or 10GBASE-LR (1310nm) for 10 gigabit Ethernet. Auto Negotiation for the port must be disabled. Customer must support 802.1Q VLANs across these connections and customer router must support Border Gateway Protocol (BGP) and BGP MD5 authentication. SAP AWS Account ID will accept incoming connection request.
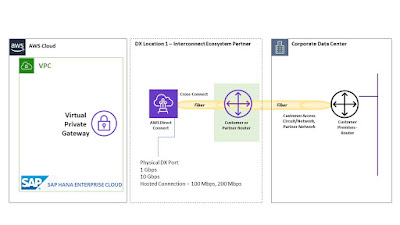
● If customers are large enterprise or public sector, they can reach out to your national carrier to provide physical connectivity from DX location through to their business premises or on-premise data center. If customer is a smaller company, they can connect AWS DX Port to their partner router and partner brings physical connectivity to customer on-premise router.
● In either case, it is a customer responsibility to bring that physical connectivity from DX Port to their on-premise router. This is just single physical fiber optic cable from AWS DX Port all the way to customer premises. While AWS DX port allocation will be faster, setting physical connection from your on-premise router to DX Router will take many weeks and this must be planned well in advance.
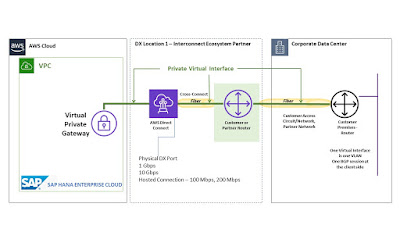
Step 3:
● Once physical connection is setup between AWS DX Port to on-premise router, virtual interface (VIF) configuration must be completed. Over the top of physical connection, multiple Virtual Interface can be created. Each VIF is considered as one VLAN. BGP peering must be established between AWS Port and Customer Router. Customer will provide BGP ASN number for establishing BGP session. SAP HANA Enterprise Cloud team will provide BGP configuration detailing ASN number, interface configuration, BGP neighbor configuration and other required routing configuration that must be completed by customer on their on-premise router.
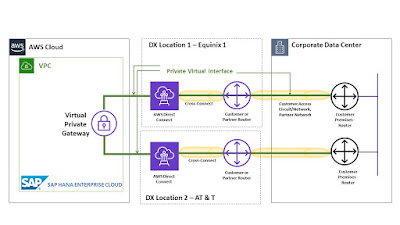
High Availability Setup:
As business critical applications run on SAP HANA Enterprise Cloud, it is important that highly resilient, fault-tolerant network connections are available. To achieve redundancy, customers can connect from multiple data center for physical data center redundancy. As a best practice two separate co-location partner can be chosen as it provides diversity in physical path and location. While building redundant links, it is also important to provision sufficient capacity to ensure that failure of one network connection does not overwhelm and degrade redundant connection.
Encryption
It is important to understand that there is no built-in or native encryption in AWS Direct Connect link. However, SAP HANA application supports application level encryption for data in transit via HTTPS/TLS1.2. Given that traffic traverse via dedicated private link and encryption is supported at the applications layer, this generally meets regulatory and compliance requirements for customers.




No comments:
Post a Comment